Vulnerability scanning in Salesforce means automatically analyzing your org’s apps, metadata, configurations, and APIs to uncover potential security risks.
But which scanning methods and tools should you use? Salesforce provides several built-in security analysis tools, with each designed for a different purpose. Understanding what each tool covers — and where they have gaps — helps you choose the right combination for comprehensive security coverage.
In this guide, we’ll break down Salesforce’s native security tools and show you where each shines, when an enterprise-grade platform like Gearset gives you the edge, and how to create a scalable vulnerability management strategy that fits seamlessly into your DevOps lifecycle.
Stop flying blind: How Truckstop brought clarity to a complex org
Vulnerability scanning methods in Salesforce
Native Salesforce security tools are built-in features that help monitor configuration, encryption, and code quality: Health Check grades your configuration settings, Shield handles encryption, and PMD flags programming mistakes. The most comprehensive scanning tool that Salesforce offers is Code Analyzer, which brings together different code-scanning engines, such as PMD, RetireJS, and ESLint, under a single umbrella to scan Apex, Visualforce, and Lightning components. Let’s look at each in a little more detail.
Salesforce Health Check
Health Check is, at its core, a pretty basic config checker. It takes your org’s current setup, compares it to Salesforce’s recommended baseline (or up to five you’ve uploaded yourself), and flags mismatches by risk level so you can tackle the most serious “High Risks” first, then work your way down to “Informational”.
What Health Check scans:
- Password policies
- Session timeout settings
- Network access controls
- Login IP rules and restrictions
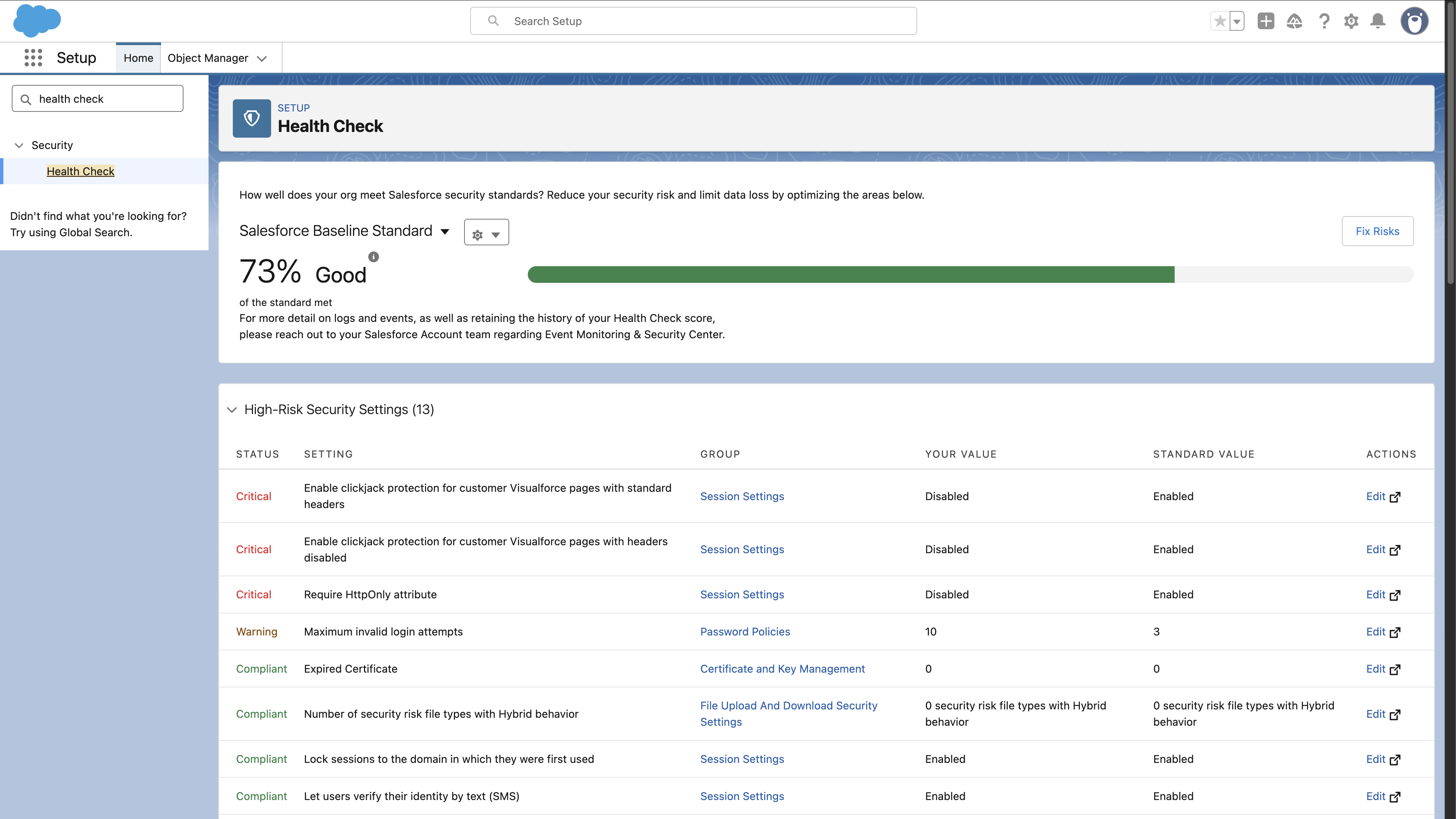
It’s easy to see why teams use Health Check. The “Fix Risks” button promises quick solutions, and the top-line score keeps stakeholders happy at a glance. But it’s important to bear in mind that Health Check doesn’t touch your code.
What Health Check doesn’t scan:
- Apex classes
- Lightning and Web Components
- Flows or Process Builders
- Custom Visualforce pages
Consider Health Check a configuration-hygiene tool only; it doesn’t provide visibility into programmatic risks such as SOQL injection or cross-site scripting. For that, you’ll need something a little more heavy duty.
Salesforce Shield
Shield Platform Encryption uses AES 256-bit encryption to keep your sensitive data safe. You can choose probabilistic encryption for the strongest protection — though it disables filtering and sorting — or deterministic encryption, which allows those features but offers slightly less security. If you want full control, Bring Your Own Key (BYOK) lets you manage the entire encryption key lifecycle yourself.
But Shield doesn’t stop at encryption. It also includes monitoring features:
- Event Monitoring tracks over 50 event types, from logins to API calls to report exports.
- Real-time streaming feeds data straight into your Security Information and Event Management (SIEM) tool of choice.
- Field Audit Trail extends your audit history from the usual 18–24 months to a full decade.
- Field tracking limits jump from 20 to 60 fields per object.
- Data Detect uses regex (pattern-matching) searches to find sensitive information like credit-card numbers or email addresses that are wrongly stored in fields or files.
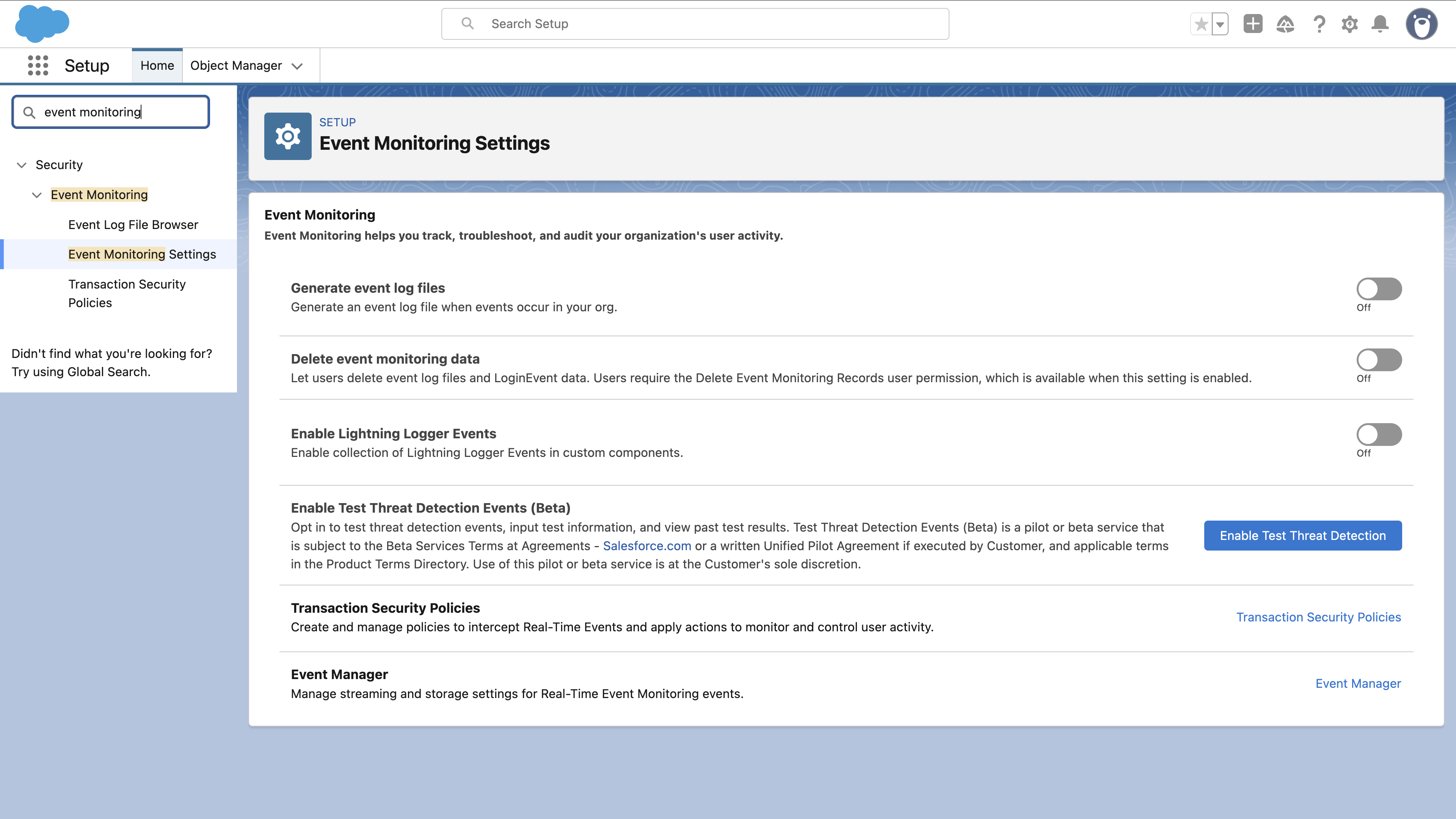
It’s a solid setup, but only protects your data, not the applications accessing it. Shield also only focuses on data-at-rest — encrypting and monitoring stored data, but not spotting or stopping vulnerabilities in the app layer.
Salesforce Code Analyzer: strengths, limits, and where it fits
PMD is great at flagging common coding mistakes in Salesforce that can cause performance issues or deployment failures, whether that’s queries placed inside loops that burn through your SOQL limit or hardcoded IDs that blow up when you switch orgs.
Salesforce saw the value of PMD and built it into their Code Analyzer CLI tool — complete with ESLint for JavaScript and a few other linters thrown in. Code Analyzer is now the go-to quality gate for AppExchange submissions.
Getting Code Analyzer up and running is fairly straightforward:
- Use IDE extensions to catch issues as you type
- Run Code Analyzer via the command line in your build scripts
- Hook Code Analyzer into your CI pipeline to automate the checks
With Code Analyzer, you get cleaner code, fewer governor limit issues, and consistent standards — core essentials for any Salesforce team. But it’s important to note that as an Application Security Testing (SAST) tool, it cannot detect runtime-specific security issues.
While Salesforce Code Analyzer does bundle general-purpose linting tools like PMD and ESLint, its real security strength comes from the integration with Salesforce Graph Engine (SFGE). SFGE goes beyond simple code checks — it follows how data moves through your code to spot hidden risks. By tracing user input all the way to where it’s used (for example, in a SOQL query or DML statement), it can catch multi-step vulnerabilities like injection risks or missing security checks that other scanners might miss.
Because it runs locally on source files, Code Analyzer uses zero API calls — a major advantage over cloud-based scanners. That means you can scan frequently in your CI/CD pipelines without affecting API limits or production performance.
The goal should be to make Code Analyzer a standard pre-deployment security gate within your pipeline. Embedding it in your workflow ensures high-risk vulnerabilities are caught and fixed before code ever reaches production.
Code Analyzer should form just one layer of a defense-in-depth strategy — complemented by dynamic testing, runtime protection, dependency scanning, manual reviews, and penetration testing. No single tool can eliminate every risk; a mature security posture relies on multiple layers working together to safeguard your Salesforce environment.
When scale breaks manual security
Most enterprise Salesforce setups aren’t neat and linear. You’ve got development, integration, UAT, staging, and production environments — and each has its own quirks: different configurations, different permissions, and different code.
Keeping security watertight across all of them with manual checks is nearly impossible. Things get missed, gaps open up, and the more environments you add, the harder it becomes to see where something’s gone wrong — let alone knowing how to fix it.
How often should I be performing vulnerability scans on my Salesforce environments?
How often you scan your environments depends on how fast you’re shipping changes. If you’re deploying daily, you’ll need scanning built right into your CI/CD flow — every commit, merge, and push. For most teams, here’s what works:
Continuous scanning (recommended):
- Every pull request gets scanned automatically
- Developers fix issues before code merges
- Security stays embedded in your workflow
Scheduled scanning (minimum baseline):
- Weekly scans for active development orgs
- Monthly scans for production
- Quarterly deep-dives for dormant orgs
But there’s a catch: manual scanning doesn’t scale. As environments multiply, small differences in configuration — like permissions or access controls — can quickly grow into major security gaps. Issues that go unnoticed in a sandbox can escalate in QA and reach production, where they expose sensitive data to real users.
Manual checks rarely keep pace with changing environments, and the cost of discovering vulnerabilities late is steep. A CRUD or FLS violation found in development is a quick fix; the same issue found in production can trigger incident response costs, compliance investigations, and deployment delays.
Building a continuous vulnerability management practice
Vulnerability management in Salesforce is an ongoing practice. The strongest security comes from embedding scanning into your existing DevOps workflow, not bolting it on as an afterthought.
The shift from reactive to proactive scanning
Most teams start scanning reactively. A penetration test finds issues. An audit flags problems. A security incident forces action. But reactive scanning means you’re always playing catch-up.
With proactive scanning:
- Vulnerabilities get caught during development, not after deployment
- Security becomes part of quality assurance, not a separate gate
- Developers learn secure coding patterns through immediate feedback
- Your security posture improves with every release
The transition requires three key elements: automated tooling that fits your pipeline, clear ownership of security tasks, and metrics that track improvement over time.
Integrating security into your DevOps pipeline
Security that slows down delivery won’t last. Your scanning needs to match your development velocity. For teams using version control and CI/CD, that means scanning at specific trigger points:
Pre-commit scanning:
- Flags issues as developers write code through IDE plugins
- Prevents bad patterns from spreading with immediate feedback
- Reinforces learning in real time
Pull request scanning:
- Catches issues before merging through automated reviews
- Builds shared accountability through team visibility
- Speeds up remediation with fix suggestions
Deployment scanning:
- Validates changes before production
- Catches configuration drift between environments
- Provides an audit trail for compliance
Each scanning point serves a purpose. Skip one, and vulnerabilities slip through. Layer them together, and you create a robust process.
How to find and fix your most critical vulnerabilities
Effective vulnerability management is about fixing the right things. Every org has limited resources, so prioritization becomes critical to maintaining both security and velocity.
How to focus on the threats that matter most
A SOQL injection in a payment flow is far more serious than a code-complexity warning in an internal report. Effective vulnerability management means focusing effort where it counts — using exploitability, impact, and context as your guide.
- Exploitability: How easily could someone take advantage of this issue?
- Impact: What would happen if it were exploited?
- Context: Where does this vulnerability live?
These factors help you triage vulnerabilities quickly and consistently:
🔴 Critical — fix immediately:
- SOQL injection vulnerabilities
- Missing CRUD/FLS checks on anything customer-facing
- Hardcoded credentials left in the code
- Cross-site scripting issues in Lightning Components
🟠 High — fix within the sprint:
- Permission bypasses in Flows
- Unescaped user input in Visualforce
- Missing error handling in integration points
- Use of deprecated APIs
🟡 Medium — schedule for next release:
- Code complexity issues
- Performance optimizations
- Clearly justified false positives
- Legacy code already on the refactor roadmap
- Issues inside third-party packages you can’t control
How to measure and prove security progress
You can’t improve what you don’t measure. Tracking the right metrics helps you prove that your security efforts are working — and justify continued investment in scanning tools.
Start with your core performance metrics:
- Mean Time to Detection (MTTD): How quickly are new vulnerabilities discovered after they’re introduced?
- Mean Time to Remediation (MTTR): Once found, how fast do they get fixed?
- Vulnerability density: Number of vulnerabilities per 1,000 lines of code — a simple measure of codebase health.
- Fix rate: Percentage of identified issues that actually get resolved.
- Recurrence rate: How often the same vulnerability patterns resurface, showing where more training or process change is needed
Then add leading indicators to track long-term improvement:
- Percentage of pull requests scanned for security issues
- Developer participation in secure coding training
- Adoption rate of secure code templates
- Use of automated fix suggestions
These metrics tell a clear story: whether your security program is actually reducing risk — or just producing more reports.
Gearset’s Code Reviews: The solution to Salesforce vulnerability scanning
Native Salesforce tools are great building blocks — but they’re siloed. Health Check focuses on configuration, Shield secures data at rest, and Code Analyzer scans code quality. What’s missing is a single, connected view that covers everything.
Gearset Code Reviews unifies those layers — scanning Apex classes, Lightning Web Components, Flows, Visualforce pages, Aura components, and permissions all mesh together. Instead of treating them like scattered bits of code, it scans the whole system as one connected setup. Every time a pull request is opened against a tracked branch, you get a fresh, automated review. Here’s what that typically covers:
- Apex classes scanned for injection vulnerabilities
- Flows checked for permission bypasses
- Lightning Web Components reviewed for XSS risks
- Visualforce pages inspected for security flaws
- Aura components validated for exposure issues
- Every metadata config is assessed for misconfigurations
Each type brings its own security headaches, and Gearset knows how to spot them all:
- Where a single manual fix might take up eight hours, Gearset gets it done in minutes.
- Salesforce-aware filtering cuts false positives significantly.
- Even your installed packages get scanned, so third-party dependencies are covered.
Best of all? Code Reviews does all this without touching your API limits. While typical org scans can chew through thousands of API calls per run, Code Reviews connects to your Git repository (GitHub, GitLab, Bitbucket, etc.) by creating webhooks for relevant events — like pull requests, merges — so it leaves your API limits untouched.
How to do security testing in Salesforce with Gearset’s Code Reviews
Security testing shouldn’t add friction to your release process — it should run alongside it. Gearset’s Code Reviews makes that possible by building automated security checks directly into the way your team already works. Every change, every pull request, every merge gets scanned automatically, so vulnerabilities are caught the moment they’re introduced, not after deployment.
The real advantage is how seamlessly Code Reviews integrates into your CI/CD pipelines. Security scans trigger automatically on every commit, with feedback delivered right inside the pull request — no manual steps, no context switching. Even Flow updates get the same protection, giving admins the same level of assurance as developers.
There are no silos between code and config — just connected, continuous scanning that keeps your entire Salesforce environment secure before anything reaches production.
Transform your security practice today
Drowning in PMD violations? Sign up for Gearset’s 30-day free trial and watch those 743 violations drop to 50 focused, fixable issues, with clear steps to fix them. You’ll get a real view of your security posture, not just another overwhelming list of warnings.
Managing complex enterprise orgs? Let’s talk. Book a demo built around your environment, and we’ll show you exactly what you stand to gain.



